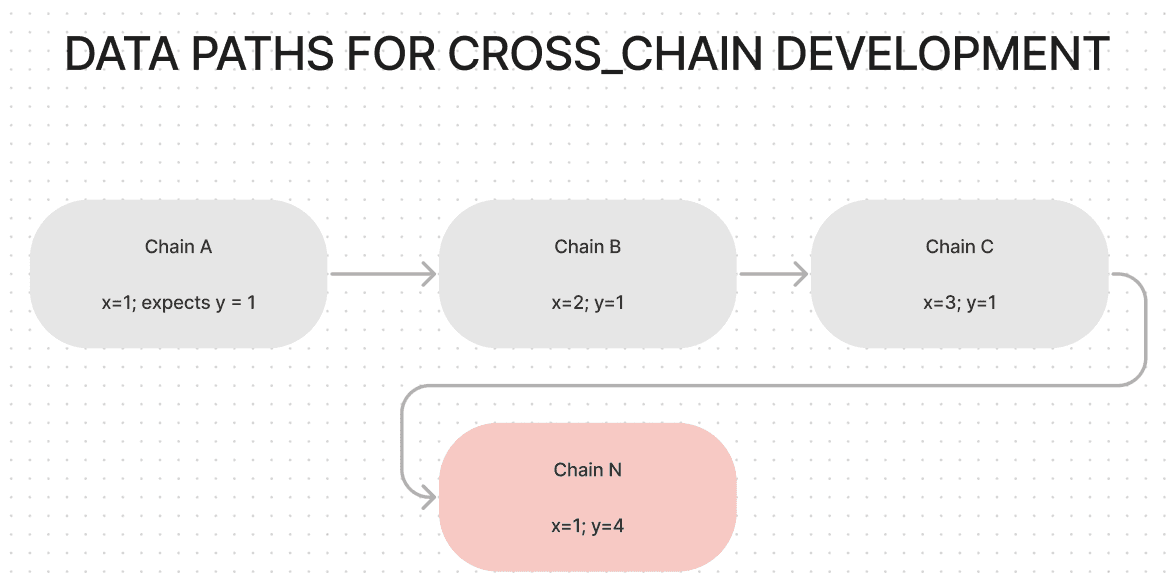
Permanent DoS of refunds through 1 wei donation
During a recent security audit of LI.FI's Eco integration, I discovered a denial-of-service (DoS) vulnerability in Eco's Vault contract that could prevent legitimate users from receiving their refunds.
Read article →